[How-To] Monitor vSphere Supervisor and Guest Clusters with VCF Operations
Monitoring vSphere Supervisor Cluster and Kubernetes Guest Cluster with the Kubernetes Management Pack in VCF (Aria) Operations.
The Monitoring is a great alternative to prometheus and grafana. No Installations necessary on the Kubernetes Guest Clusters.
Goal
The Goal is to monitor the vSphere Supervisor Cluster and every Kubernetes Guest Cluster, also monitoring newly provisioned Guest Clusters automatically.

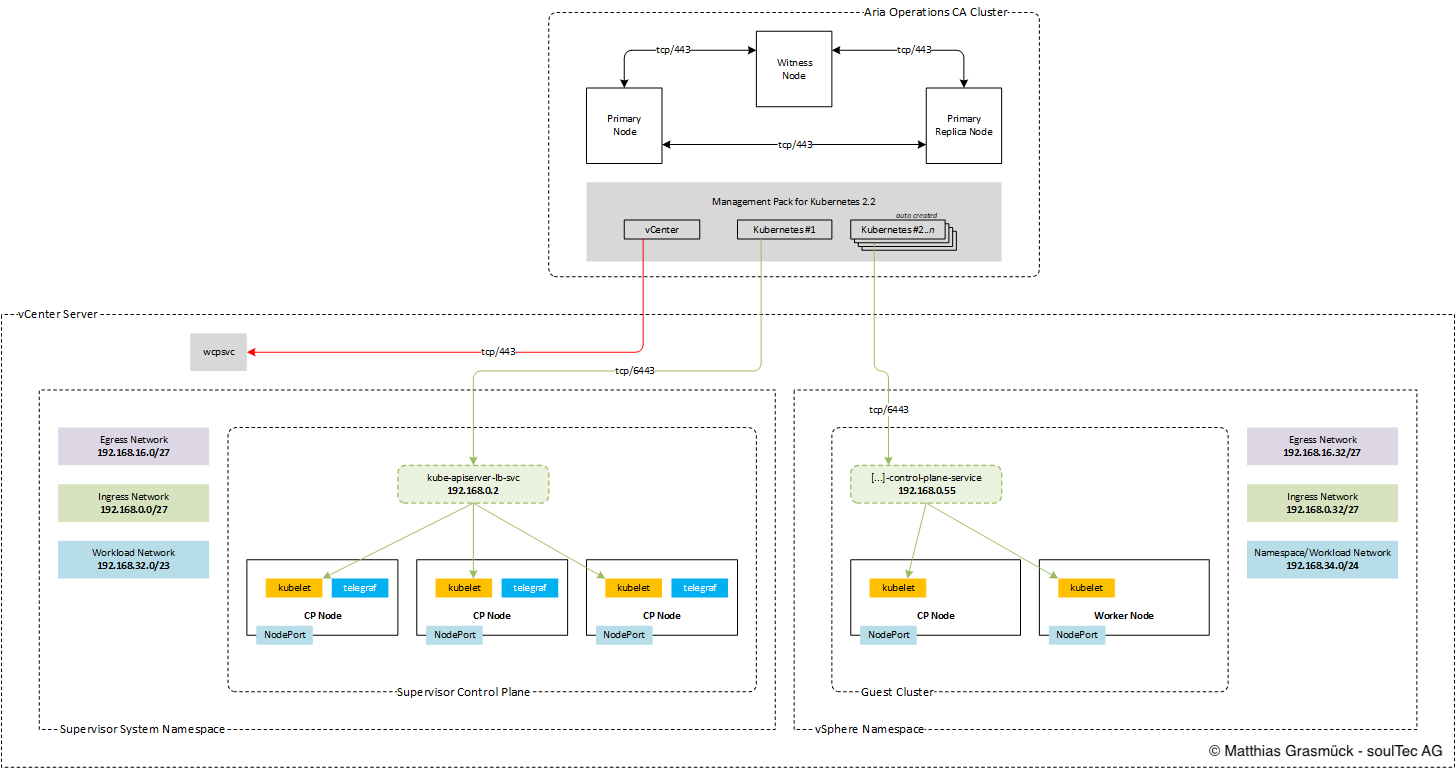
Logical Diagram
The Kubernetes Management Pack works the following way:
Prerequisites
- Aria Operations 8.18.x
- Kubernetes Management Pack (2.2)
- vCenter already added in Aria Ops
Gather Required Data
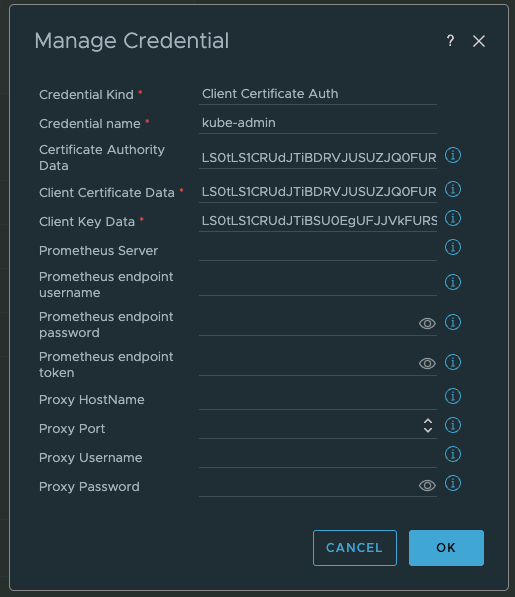
We need the following Data to configure a Account on the Aria Operations Kubernetes Management Pack:
- Supervisor IP (VIP)
- certificate-authority-data
- client-certificate-data
- client-key-data
Step 1 – SSH Login to Control Plane Nodes
SSH to the vCenter Appliance with the root user, then run (bash shell):
sshpass -p `/usr/lib/vmware-wcp/decryptK8Pwd.py | \
grep PWD | \
awk '{print $2}'` ssh -o StrictHostKeyChecking=no root@`/usr/lib/vmware-wcp/decryptK8Pwd.py | \
grep IP | \
awk '{print $2}'`
If the bash shell is not enabled, run:
shell.set --enabled=true
View the kubeconfig file on one of the CP Nodes an gather the following data:
- certificate-authority-data
- client-certificate-data
- client-key-data
cat ~/.kube/config
Aria Operations
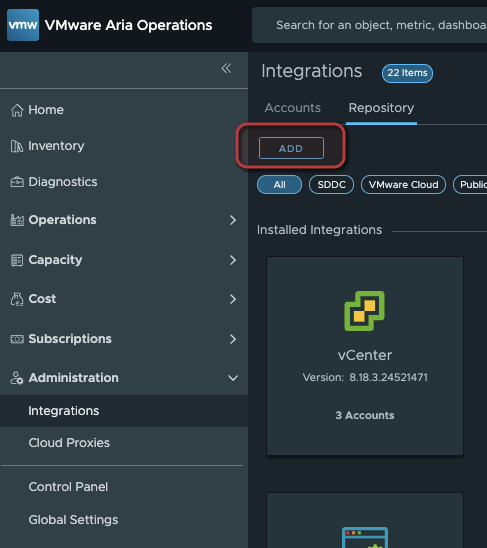
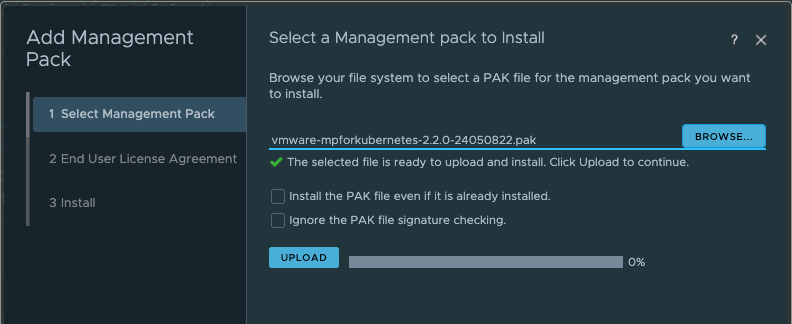
Add the Kubernetes Management Pack (.pak) File
Administration > Integrations > Repository
Add the Supervisor Cluster
Administration > Integrations > Add Cloud Account > Kubernetes
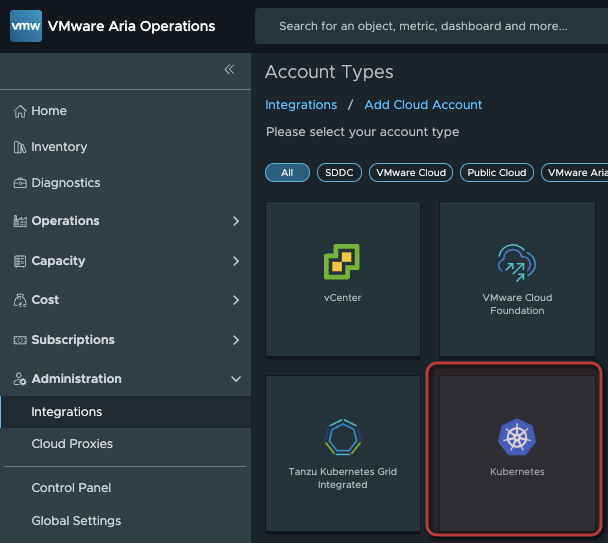
- Control Plane URL: Supervisor VIP
- Kubelet
- Advanced Settings: Autodiscover TGK Guest Cluster (vCenter needs to be added to Aria Ops already)

Credentials:
Inventory
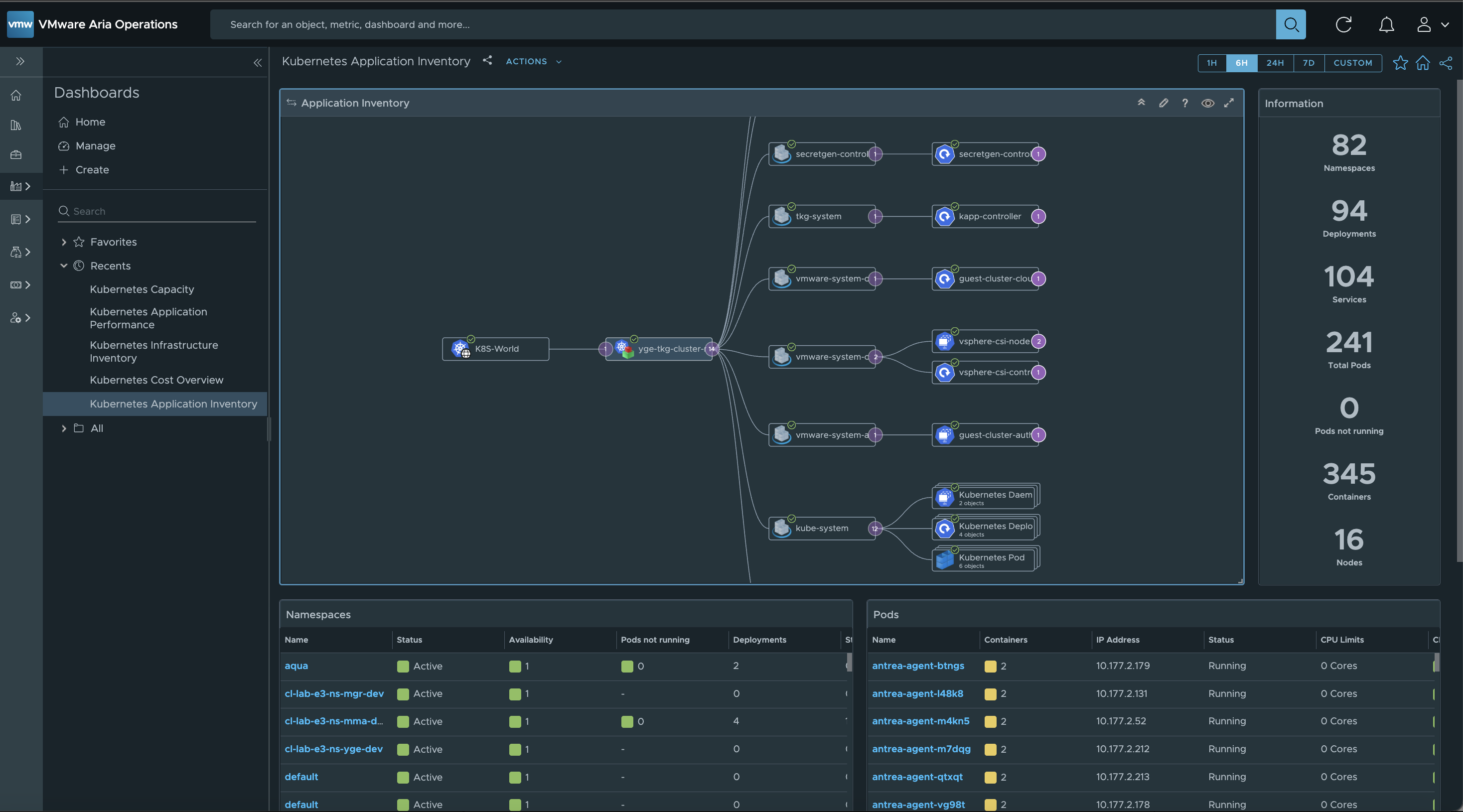
If Autodiscovery is enabled, your Kubernetes Guest Clusters will show up after a few minutes.

Dashboards
The Kubernetes Management Pack includes lots of useful dashboards to explore.










Leave a Reply